2025
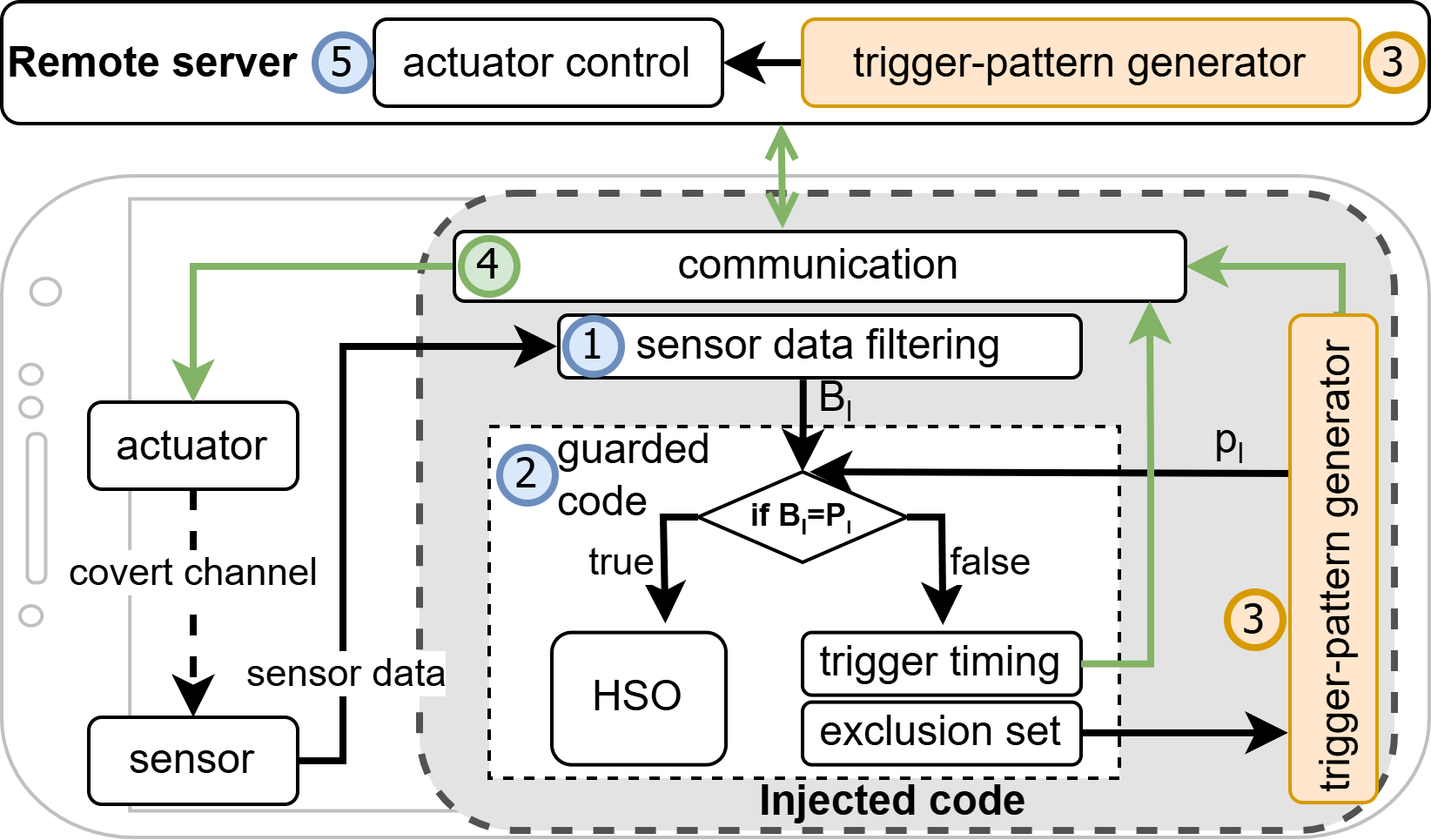
Beyond Conventional Triggers: Auto-Contextualized Covert Triggers for Android Logic Bombs
Ye Wang, Bo Luo, Fengjun Li
Network and Distributed System Security Symposium (NDSS)Accepted. 2026
In this paper, we present SensorBomb, a logic-bomb framework that violates this assumption by auto-contextualizing triggers within an app’s legitimate sensor usage, actuator behaviors, and functional context, using onboard sensor–actuator covert channels and dynamically adapted trigger patterns to evade analysis, fuzzing, anomaly detection, and user suspicion.
Beyond Conventional Triggers: Auto-Contextualized Covert Triggers for Android Logic Bombs
Ye Wang, Bo Luo, Fengjun Li
Network and Distributed System Security Symposium (NDSS)Accepted. 2026
In this paper, we present SensorBomb, a logic-bomb framework that violates this assumption by auto-contextualizing triggers within an app’s legitimate sensor usage, actuator behaviors, and functional context, using onboard sensor–actuator covert channels and dynamically adapted trigger patterns to evade analysis, fuzzing, anomaly detection, and user suspicion.
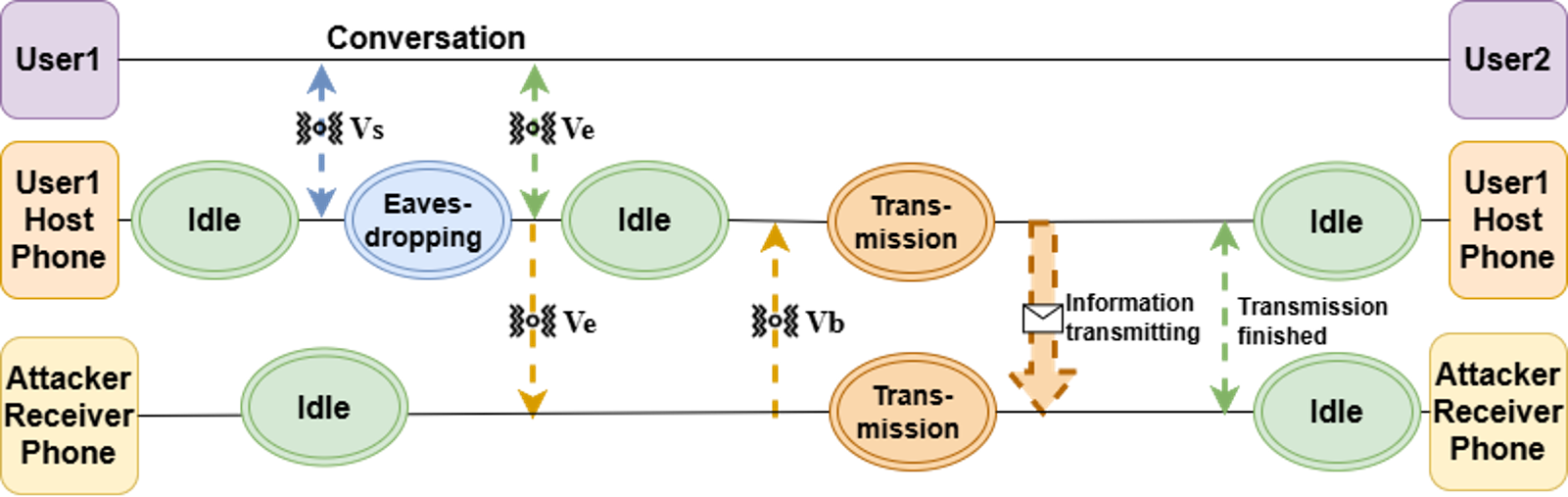
Poster: A Novel Fully Sensor-driven Attack Chain.
Ye Wang, Bo Luo, Fengjun Li
Annual Computer Security Applications Conference (ACSAC). 2025
In this paper, we highlight the renewed feasibility of motion sensor-based side- and covert-channel attacks under modern Android restrictions.
Poster: A Novel Fully Sensor-driven Attack Chain.
Ye Wang, Bo Luo, Fengjun Li
Annual Computer Security Applications Conference (ACSAC). 2025
In this paper, we highlight the renewed feasibility of motion sensor-based side- and covert-channel attacks under modern Android restrictions.
2024
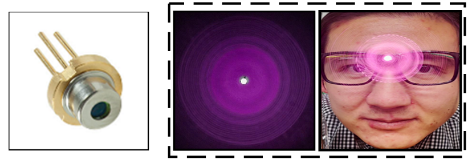
The Invisible Polyjuice Potion: an Effective Physical Adversarial Attack against Face Recognition
Ye Wang, Zeyan Liu, Bo Luo, Rongqing Hui, Fengjun Li
Proceedings of the 2024 on ACM SIGSAC Conference on Computer and Communications Security (CCS) 2024
In this paper, we propose a novel physical adversarial attack against deep face recognition systems, namely Agile (Adversarial Glasses with Infrared LasEr). It generates adjustable, invisible laser perturbations and emits them into the camera CMOS to launch dodging and impersonation attacks against facial biometrics systems.
The Invisible Polyjuice Potion: an Effective Physical Adversarial Attack against Face Recognition
Ye Wang, Zeyan Liu, Bo Luo, Rongqing Hui, Fengjun Li
Proceedings of the 2024 on ACM SIGSAC Conference on Computer and Communications Security (CCS) 2024
In this paper, we propose a novel physical adversarial attack against deep face recognition systems, namely Agile (Adversarial Glasses with Infrared LasEr). It generates adjustable, invisible laser perturbations and emits them into the camera CMOS to launch dodging and impersonation attacks against facial biometrics systems.
2023
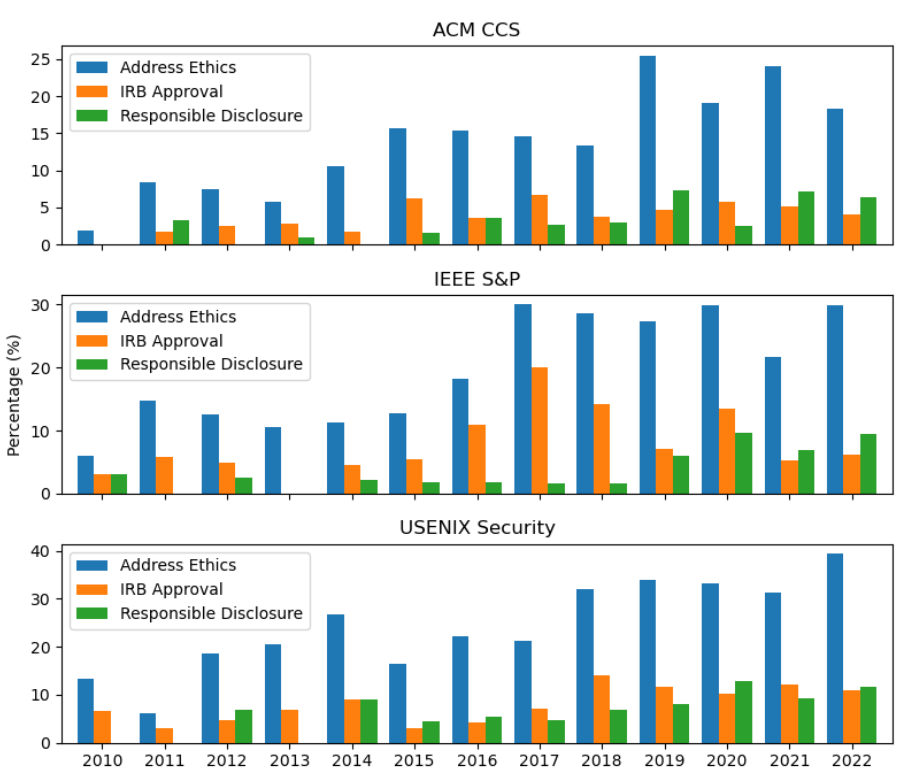
Poster: Ethics of Computer Security and Privacy Research Current Status and Trends from a Data Perspective
Kevin Li, Zhaohui Wang, Ye Wang, Bo Luo, Fengjun Li
Proceedings of the 2023 ACM SIGSAC Conference on Computer and Communications Security 2023
Ethics is an important criterion for security research. This work presents the current status and trends that security researchers have taken to address ethical concerns in their studies from a data perspective.
Poster: Ethics of Computer Security and Privacy Research Current Status and Trends from a Data Perspective
Kevin Li, Zhaohui Wang, Ye Wang, Bo Luo, Fengjun Li
Proceedings of the 2023 ACM SIGSAC Conference on Computer and Communications Security 2023
Ethics is an important criterion for security research. This work presents the current status and trends that security researchers have taken to address ethical concerns in their studies from a data perspective.
2015
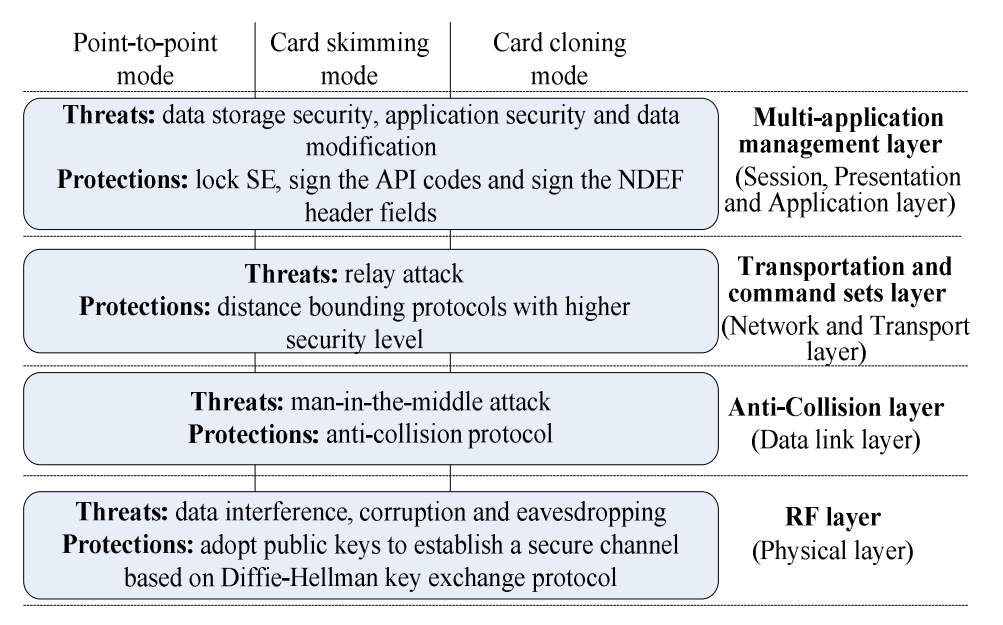
A Near Field Communication(NFC) Security Model Based on OSI Reference Model
Wei Fan, Weiqing Huang, Zhujun Zhang, Ye Wang, Degang Sun
2015 IEEE Trustcom/BigDataSE/ISPA 2015
This paper sets up an NFC security model based on the OSI model. Security risk and countermeasure of each layer of the security model are described as the foundation of the former works. Evaluation methods are proposed to assess the security model, and the results show a high protection level.
A Near Field Communication(NFC) Security Model Based on OSI Reference Model
Wei Fan, Weiqing Huang, Zhujun Zhang, Ye Wang, Degang Sun
2015 IEEE Trustcom/BigDataSE/ISPA 2015
This paper sets up an NFC security model based on the OSI model. Security risk and countermeasure of each layer of the security model are described as the foundation of the former works. Evaluation methods are proposed to assess the security model, and the results show a high protection level.