
 University of Kansas
University of Kansas
I am a final-year PhD candidate in Computer Science at the University of Kansas, advised by Dr. Fengjun Li and Dr. Bo Luo.
My research has been a continuous journey to understand how security connects sensing, communication, and artificial intelligence across the digital and physical worlds.
My research interests include:
• Trustworthy and privacy-preserving ML/AI: Adversarial ML; Prompt injection; AI misinformation and misuse.
• CPS/Mobile security and privacy: Covert and side channels; Sensor-driven adversarial perception; Privacy protection.
• Communication security: NFC; Optical fiber communication; UAV navigation and control-link.
Before joining KU, I received my B.Eng. and M.Eng. degrees from Beihang University, where I was advised by Prof. Xiaxiao Wang. After graduation, I worked as a full-time research scientist at the Institute of Information Engineering, Chinese Academy of Sciences, under the supervision of Prof. Weiqing Huang and Prof. Meng Zhang.
News | Education | Research Experience | Honors & Awards | Teaching Experience | Selected Publications
Warning
Problem: The current name of your GitHub Pages repository ("Solution: Please consider renaming the repository to "
http://".
However, if the current repository name is intended, you can ignore this message by removing "{% include widgets/debug_repo_name.html %}" in index.html.
Action required
Problem: The current root path of this site is "baseurl ("_config.yml.
Solution: Please set the
baseurl in _config.yml to "News
Education
-
 University of KansasDepartment of Electrical Engineering and Computer Science
University of KansasDepartment of Electrical Engineering and Computer Science
Ph.D. Candidate in Computer ScienceJan. 2020 - present -
 Beihang UniversitySchool of Instrumentation Science and Optoelectronic Engineering
Beihang UniversitySchool of Instrumentation Science and Optoelectronic Engineering
M.Eng. in Optical EngineeringSep. 2011 - Mar. 2014 -
 Beihang UniversitySchool of Instrumentation Science and Optoelectronic Engineering
Beihang UniversitySchool of Instrumentation Science and Optoelectronic Engineering
B.S. in Electronic EngineeringSep. 2007 - Jul. 2011
Research Experience
-
 Institute for Information Science (I2S), University of Kansas(KU)Graduate Research AssistantJan. 2020 - present
Institute for Information Science (I2S), University of Kansas(KU)Graduate Research AssistantJan. 2020 - present -
 Institute of Information Engineering (IIE), Chinese Academy of Sciences (CAS)Assistant Research FellowMar. 2014 - Dec. 2019
Institute of Information Engineering (IIE), Chinese Academy of Sciences (CAS)Assistant Research FellowMar. 2014 - Dec. 2019 -
 Institute of Optoelectronics Technology, Beihang UniversityGraduate Research AssistantSep. 2011 - Mar. 2014
Institute of Optoelectronics Technology, Beihang UniversityGraduate Research AssistantSep. 2011 - Mar. 2014
Selected Honors & Awards
-
Internet Society NDSS Fellowship - Internet Society2026
-
Doctoral Student Research Fund Award - KU2025
-
DAVID D. and MILDRED H. ROBB AWARD - KU2024, 2025, 2026
-
ACM CCS Travel Grant Award - ACM SIGSAC2024
-
Graduate Engineering Association Award - KU2024, 2025
-
Graduate Student Travel Fund - KU Student Senate2024, 2025
-
The second prize of the Science and Technology Award - MIIT (PRC)2019
-
Excellent Researcher - IIE, CAS2018
-
Excellent Researcher - 4th research department, IIE, CAS2016
-
Outstanding Master’s Thesis Award - Beihang University2014
-
Science and Technology Award - Ministry of Education (PRC)2013
-
Graduate Guanghua Scholarship - Beihang University2013
-
Outstanding Undergraduate Thesis Award - Beihang University2011
Teaching Experience
-
EECS 569 - Computer ForensicsFall 2024
-
EECS 565 - Introduction to Information and Computer SecurityFall 2025, 2024, 2023
-
EECS 447 - Introduction to Database SystemsSpring 2026, 2024, 2023
-
EECS 268 - Programming IISpring 2025
Selected Publications (view all )
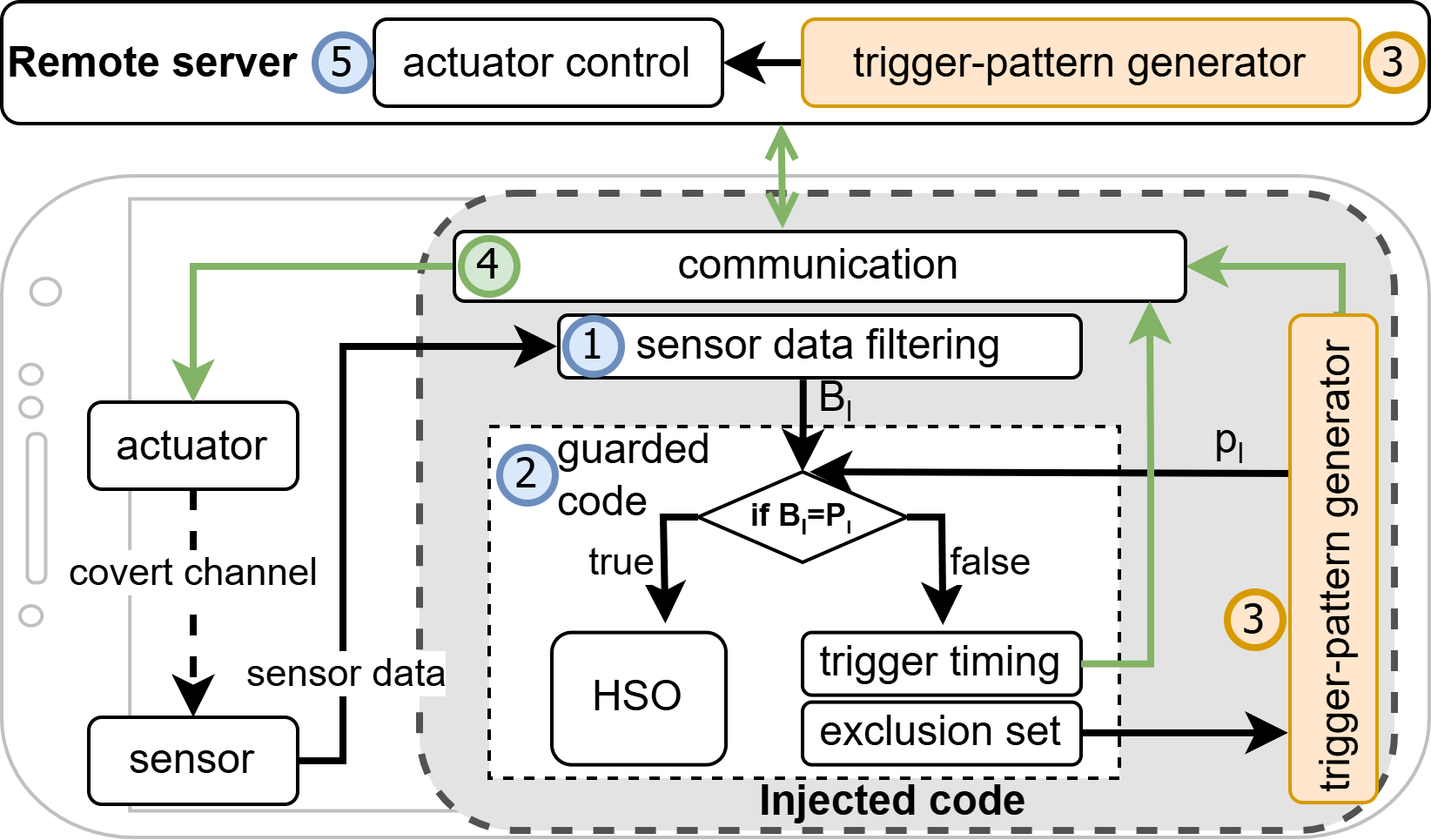
Beyond Conventional Triggers: Auto-Contextualized Covert Triggers for Android Logic Bombs
Ye Wang, Bo Luo, Fengjun Li
Network and Distributed System Security Symposium (NDSS)Accepted. 2026
In this paper, we present SensorBomb, a logic-bomb framework that violates this assumption by auto-contextualizing triggers within an app’s legitimate sensor usage, actuator behaviors, and functional context, using onboard sensor–actuator covert channels and dynamically adapted trigger patterns to evade analysis, fuzzing, anomaly detection, and user suspicion.
Beyond Conventional Triggers: Auto-Contextualized Covert Triggers for Android Logic Bombs
Ye Wang, Bo Luo, Fengjun Li
Network and Distributed System Security Symposium (NDSS)Accepted. 2026
In this paper, we present SensorBomb, a logic-bomb framework that violates this assumption by auto-contextualizing triggers within an app’s legitimate sensor usage, actuator behaviors, and functional context, using onboard sensor–actuator covert channels and dynamically adapted trigger patterns to evade analysis, fuzzing, anomaly detection, and user suspicion.
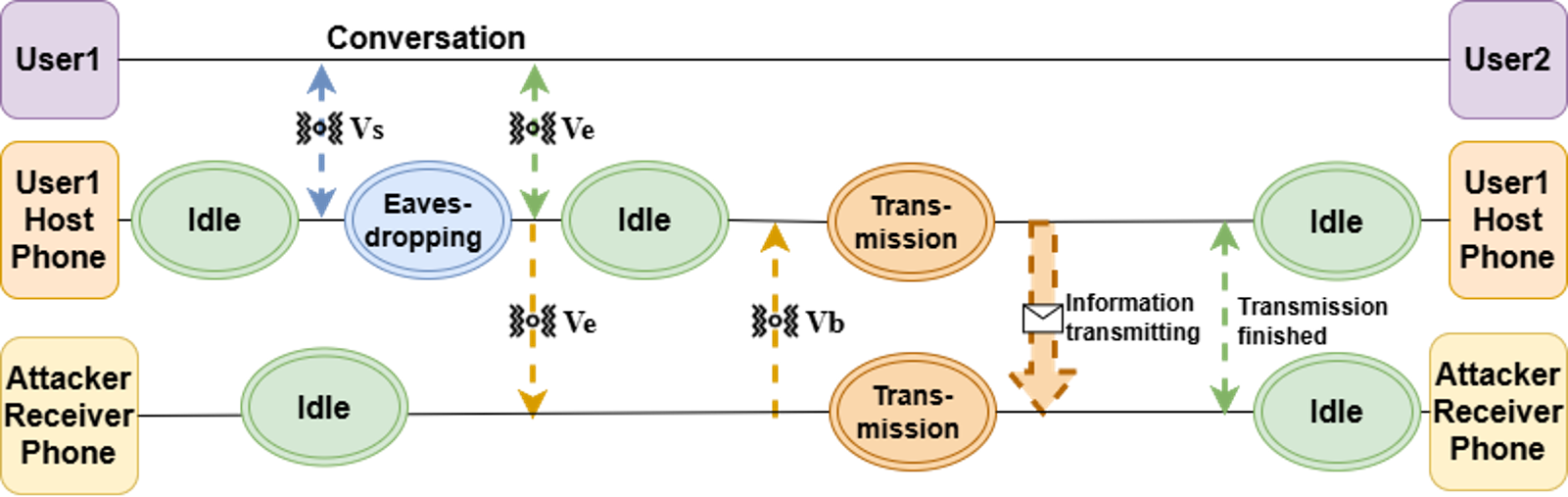
Poster: A Novel Fully Sensor-driven Attack Chain.
Ye Wang, Bo Luo, Fengjun Li
Annual Computer Security Applications Conference (ACSAC). 2025
In this paper, we highlight the renewed feasibility of motion sensor-based side- and covert-channel attacks under modern Android restrictions.
Poster: A Novel Fully Sensor-driven Attack Chain.
Ye Wang, Bo Luo, Fengjun Li
Annual Computer Security Applications Conference (ACSAC). 2025
In this paper, we highlight the renewed feasibility of motion sensor-based side- and covert-channel attacks under modern Android restrictions.
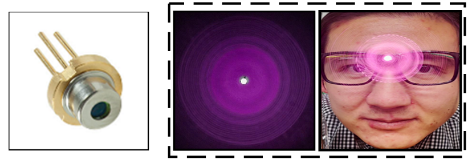
The Invisible Polyjuice Potion: an Effective Physical Adversarial Attack against Face Recognition
Ye Wang, Zeyan Liu, Bo Luo, Rongqing Hui, Fengjun Li
Proceedings of the 2024 on ACM SIGSAC Conference on Computer and Communications Security (CCS) 2024
In this paper, we propose a novel physical adversarial attack against deep face recognition systems, namely Agile (Adversarial Glasses with Infrared LasEr). It generates adjustable, invisible laser perturbations and emits them into the camera CMOS to launch dodging and impersonation attacks against facial biometrics systems.
The Invisible Polyjuice Potion: an Effective Physical Adversarial Attack against Face Recognition
Ye Wang, Zeyan Liu, Bo Luo, Rongqing Hui, Fengjun Li
Proceedings of the 2024 on ACM SIGSAC Conference on Computer and Communications Security (CCS) 2024
In this paper, we propose a novel physical adversarial attack against deep face recognition systems, namely Agile (Adversarial Glasses with Infrared LasEr). It generates adjustable, invisible laser perturbations and emits them into the camera CMOS to launch dodging and impersonation attacks against facial biometrics systems.
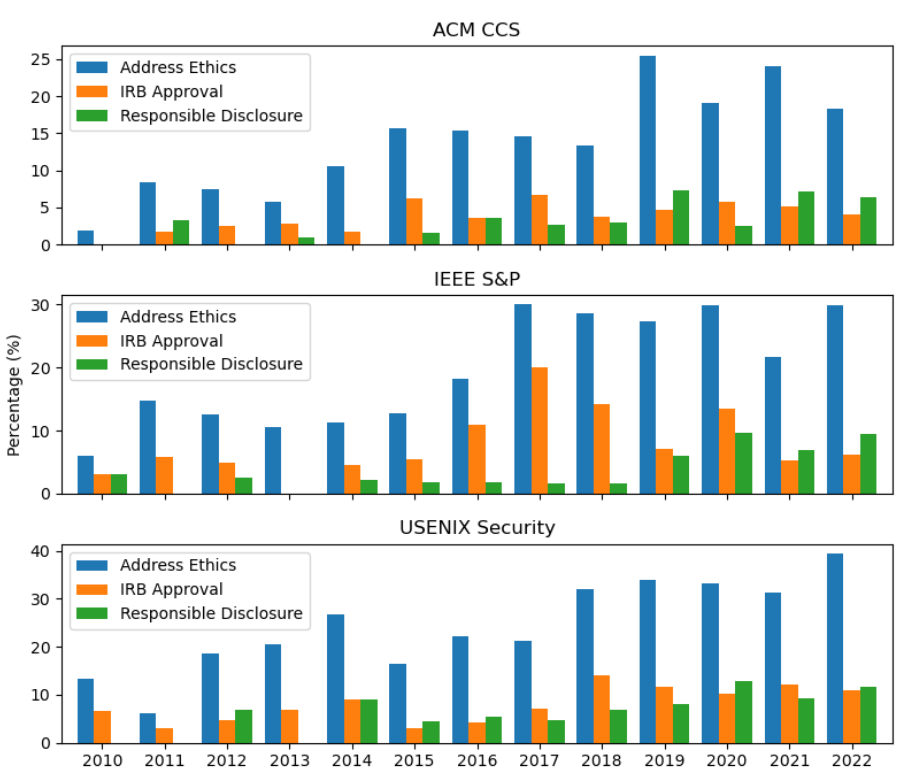
Poster: Ethics of Computer Security and Privacy Research Current Status and Trends from a Data Perspective
Kevin Li, Zhaohui Wang, Ye Wang, Bo Luo, Fengjun Li
Proceedings of the 2023 ACM SIGSAC Conference on Computer and Communications Security 2023
Ethics is an important criterion for security research. This work presents the current status and trends that security researchers have taken to address ethical concerns in their studies from a data perspective.
Poster: Ethics of Computer Security and Privacy Research Current Status and Trends from a Data Perspective
Kevin Li, Zhaohui Wang, Ye Wang, Bo Luo, Fengjun Li
Proceedings of the 2023 ACM SIGSAC Conference on Computer and Communications Security 2023
Ethics is an important criterion for security research. This work presents the current status and trends that security researchers have taken to address ethical concerns in their studies from a data perspective.